Honeypot Concepts
People often wonder what honeypots can be used
for. Here are some examples on how Honeyd and honeypots in general can be
used to improve security or for network measurements.
Wireless Honeypot
Setup an isolated machine running Honeyd:
- Run an access point. This can be done with Linux or *BSD by
putting a wireless card into
hostap mode and using it
to create a wireless network.
- Configure and run a
DHCP server. You need to
determine which network the DHCP server should hand addresses out
for, e.g. 192.168.0.0/16. The router and name server
records need to to point to IP addresses simulate by Honeyd.
- Instrument Honeyd to provide fake
Internet topology. This can be achieved by configuring a
virtual network topology for the whole IP address space except for
the address range that is served by DHCP. Make sure that you have
a name server running that resolves names. This can be done
without the laptop being connected to the Internet itself.
|
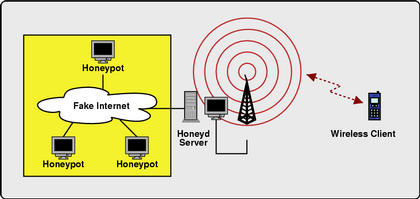
Diagram showing wireless honeypot
configuration. |
Monitor for
unauthorized access:
- Run an intrusion detection system or monitor services for abuse or
interesting activity.
- Set up spam traps and open proxies to see if spammers use unsecured
wireless access points to send spam.
Integrated Honeypots
Distract adversaries by mixing virtual honeypots into
your production network:
- Use either Arpd
or a recent version of Honeyd with ethernet-level simulation to
redirect traffic for unused IP addresses. Ethernet-level
simulation can be turned on by using:
set template ethernet
"00:aa:bb:cc:dd:ee"
- Set up Honeyd to simulate virtual honeypots for the redirected
IP addresses.
Monitor for unauthorized access:
- Run an intrusion detection system or monitor services for
abuse or interesting activity.
- Detect compormised machines by watching who probes the
honeypots.
Just by running honeypots, you make live harder
for adversaries because they might waste their resources by breaking
into the honeypots. Honeypots can also serve as a warning sign for a
highly monitored network. |
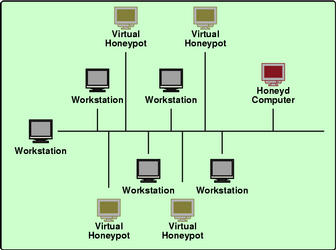
Diagram showing an integrated honeypot
configuration. |
If you are missing a concept, please let me know.


