The difference between this (a primer) and an FAQ, is that most FAQ's, in practice, tend to be question-and-answer oriented, and generally seem to try to cover ALL issues, not just the ones frequently asked about. This primer is intended as a starting point for someone who has an interest in the subject, but doesn't know where to start or what questions to ask. This should also help to broaden the understanding of people who have worked with TCP/IP for a while, but either haven't had the time to study all the less-than-useful theory behind the subject, or have been somewhat overwhelmed by the many theoretical details and have missed the big picture.
This is maintained in HTML. I have made it available as one large page for the benefit of those who prefer to print off a copy and read it that way. Also useful for sharing via hard copy. If you choose to print this out and distribute this, I ask that you distribute it in its entirety, and that you don't charge for it.
Feedback, of course, is always greatly appreciated, and will help determine the direction and growth of this living document. In fact, just a quick email to say "thanks" (if it helped) will help motivate me to keep this current and expanding :-)
| Ethernet Topologies | |||
|---|---|---|---|
| Pro | Con | Typical Use | |
| 10BaseT | *Very reliable- one fault usually doesn't affect entire network. | *Relatively short distance from hub to workstation
(100m). *Requires a lot of wiring (a separate link for each workstation.) |
*Offices and home networks. |
| 10Base2 | *Cheap- no hub required, no wiring except from station to
station. *Well shielded against electrical interference. *Can transmit longer distances (200m). |
*Any break in connectivity disrupts entire network
segment. *Problems can be very difficult to troubleshoot. |
*Small or home networks, hub to hub links. |
| 10BaseF | *Long distance networking (2000m). *Immune to electrical interference. |
*Very expensive to install. | *Long distance hub-to-hub or switch-to-hub links. |
Ethernet is like a bunch of loud people in an unmoderated meeting room. Only
one person can talk at a time, because communication consists of standing up and
yelling at the top of your lungs. People are allowed to start communicating
whenever there is silence in the room. If two people stand up and start yelling
at the same time, they wind up garbling each others' attempt at communication,
an event known as a "collision." In the event of a collision, the two offending
parties sit back down for a semi-random period of time, then one of them stands
up and starts yelling again. Because it's unmoderated, the likelihood of
collisions occurring increases geometrically as the number of talkers and the
amount of stuff they talk about increases. In fact, networks with many
workstations are generally considered to be overloaded if the segment
utilization exceeds 30-40%. If the collision light on your hubs is lit more
often than not, you probably need to segment your network. Consider the purchase
of a switch, described below.
Ethernet hubs are used in 10BaseT networks.
A standard hub is just a dumb repeater-- anything it hears on one port, it
repeats to all of its other ports. Although 10BaseT is usually wired with eight
wire jacks (known as RJ45 connectors), only four wires are used-- one pair to
transmit data, and another pair to receive data. While transmitting, an Ethernet
card will listen to its receive pair to see if it hears anyone else talking at
the same time. These two behaviors (listen for silence before talking, and
detect other people talking at the same time) are described by the acronym people as CSMA/CD, or
"Carrier Sense Multiple Access, Collision Detection."
One hundred
megabit Ethernet (100BaseTX) works just like ten megabit Ethernet, only ten
times faster. On high-quality copper (known as Category 5, or CAT 5 UTP),
100BaseTX uses the same two pair of copper to communicate. If you have standard
network-quality copper, an alternative is to use 100BaseT4, which uses all four
pairs, but can communicate at 100Mbps on CAT 3 UTP.
Gigabit Ethernet
works just like hundred megabit Ethernet, only ten times faster (1000Mbps, or
1Gbps.) There are some Gigabit Ethernet devices floating around out there, but
it's unlikely that you'll find such devices on the small LANs that you'd find on
the "Near Side of the 'Net."
If your conference room gets too busy, you
may consider splitting them into two groups by putting a partition wall with a
door between the halves, and putting a person in the doorway. This person would
listen to the conversations in both rooms, memorize the names (Ethernet card
addresses) of everyone in each room, and forward messages from room to room when
necessary. A device to do this is called a "transparent bridge." It's called
"transparent" because it's smart enough to learn the Ethernet addresses on its
own without the workstations suspecting anything is going on. ["Source-route
bridges" are uncommonly used so I'm not going to discuss them.]
Ethernet
switches are little more than high-speed, multi-port bridges. They learn the
Ethernet addresses of everyone attached to each port, and make intelligent
forwarding decisions based on Ethernet card address (aka MAC address.) Because
communication between 100Mbps and 10Mbps networks requires buffering, Ethernet
switches are often used for this purpose. Many inexpensive switches have many
10Mbps ports and one or two 100Mbps ports. Typically, you would connect your
server(s) to the 100Mbps port(s), and workstations or entire hubs to the 10Mbps
ports. The buffering and intelligent forwarding allows another interesting
feature to exist-- "full-duplex" Ethernet. "Half-duplex" means you can either
talk or listen, but not both, at a given time, such as when using a radio.
"Full-duplex" communication means you can talk and listen at the same time, such
as when on the phone. Since 10BaseT uses separate pairs of copper for sending
and receiving, it's physically possible to do both if there are no other
workstations on your network segment-- which is the case if you are directly
attached to a switch. Note that both the switch port and your network card must
be configured for full duplex operation for this to work, but the result is
worth it: a full 20Mbps for "regular" Ethernet and a whopping 200Mbps of
bandwidth available for full-duplex fast Ethernet. Since collisions are
eliminated, the 30% rule does not apply. When considering the purchase of a
switch, there are a few important considerations, not all of which may apply to
your requirements:
| Layer | Name | Protocols / Terms | Devices that operate in this layer | Addresses are called... |
| 3 | Network | IP, IPX, AppleTalk | Routers | Network Addresses |
| 2 | Datalink | Ethernet, Token Ring, PPP, SLIP, HDLC | Bridges, Switches, Repeaters, Hubs | Datalink, or MAC* addresses |
| 1 | Physical | Unshielded Twisted Pair, Shielded Twisted Pair, Coax, Twinax, Serial cable | Modems, CSU/DSUs | N/A (cables don't have addresses) |
*MAC, in this case, stands for Media Access Control, not to be confused with an address for a Macintosh...
Combinations that include a term from each layer describe fully how a packet is getting from a given point "A" to a directly connected point "B". For example, A may be talking to B using IP over Ethernet over Unshielded Twisted Pair; or, "my computer talks to my ISP using IP over PPP over a serial cable" (a modem is simply a serial cable extender in this sense.) From the physical layer standpoint, devices have no addresses. On the datalink layer, all Ethernet and Token Ring cards all have 6-byte addresses manufactured into them, called MAC addresses (nothing to do with Macintoshes.) Point-to-point links such as serial lines do not have MAC addresses, which creates special cases from a data transmission standpoint, that are outside the scope of this document.
The Physical layer defines the electrical media and signaling used to transmit information on a wire (or wires.) The datalink layer defines the format of the data as it is transmitted (e.g., an Ethernet frame.) Network layer information is encapsulated inside datalink layer frames. If you look at an IP packet on an Ethernet wire it would look something like this:
| Ethernet Header (with dest and src MAC addr) | IP Header (with dest and src IP addr, and checksum) | Actual Data |
Note that this indicates that, in order for two Ethernet-attached stations to communicate with each other via IP, they must know the MAC address of each other. If station "A" knows the IP address of station "B", and knows station "B" is on the same subnet, station "A" will issue an Address Resolution Protocol (ARP) broadcast. An ARP broadcast is a message that says, "Who out there is 192.168.1.1?" The TCP/IP software running on the workstation or router at 192.168.1.1 is responsible for sending back an ARP response that says, "I am 192.168.1.1, and my MAC address is 08:00:09:AF:24:33." All stations keep an ARP cache with the MAC and IP addresses of all the stations it recently communicated with directly. Try the command "arp -a" sometime on a UNIX or Windows workstation; on a Cisco router, the command is "show arp".
Note that layer 1 devices are "invisible" to layer 2; and layer 2 devices are "invisible" to layer 3. In other words, TCP/IP doesn't care if you're running over Ethernet or Token Ring, as long as it's connected properly. In fact, you can put bridging and/or switching devices on your network without disturbing any of your IP subnetting. Similarly, you can convert between different types of media (e.g., coax to twisted pair) without any layer 2 devices being aware of the change. To change layer 1 media, you typically need a layer 2 device (e.g., "I have a Ethernet Coax to Ethernet Twisted-Pair repeater".) To change the layer 2 protocol (e.g., Ethernet to Token Ring) you typically need a layer 3 device (a router.) All this is good, since it allows some measure of media independence within the network; you can run IP over just about anything better than two cans and a string, and even that, if you can find transceivers to handle it ;-)
The four items you need to use IP effectively on the Internet (that you don't need to set up an IPX workstation) are the IP Address, the IP Subnet Mask, the IP Address of the Default Router, and the IP Address(es) of your Domain Name Servers (DNS Servers, often shortened to "Name Servers.")
IP Addresses: IP uses 4-byte addresses, like 192.168.1.1. IPX uses 10-byte addresses, like 10000001:0000C04C1141. Those happen to be the IP and IPX addresses of the workstation I'm using now. "But wait," you ask, "I've used IPX before and all it uses are four byte addresses." Well, that's not entirely correct. The 4-byte "IPX Address" configured into IPX-based servers is only the network portion of the address. All addresses used by routable protocols have a "network" portion, which gets your packet to your nearest router, and a "host" portion, which indicates which host station you are on that routed segment. The 4-byte "IPX Address" you define is actually a 4-byte "IPX Network Address." The other 6 bytes is the hardware address of your NIC. Since IP addresses don't use the unique hardware address of your NIC, you must define them manually (or semi-manually by configuring a BOOTP or DHCP server, a task which is currently outside the scope of this document.)
IP Subnet Masks: Subnet masks (described in more detail in the next section) are used in IP to determine which part of the four-byte IP address describes the network you're on, and which part describes which host you are on that network segment. In IPX, the first four bytes always indicate the network you're on, and your six byte MAC layer address indicates which host you are on the network segment. In IP, the portions used to describe which network you're on can range from the first 8 bits of the address, to including all except the last two bits of the whole address. More in the next section.
Default Router: In IPX, routers are identified by sending out a broadcast that says, in essence, "Hey? Who out here is a router?" In IP, there has historically NOT been any automatic method for router discovery. There is now a protocol for IP router discovery, but it is not widely implemented. Therefore, you must tell the workstation what the address of the local router is. Note that with end-station PPP (like Win95 Dial-Up Networking), the default route is automatically set to, "out the serial cable." You do not need to set more than one default route. If the default router feels the packet would reach a destination better through a different router, the default router will tell your IP stack to use the other router (this is an ICMP Redirect.) If you specify no default route, no packets from that workstation can make it off the local wire; therefore, it is better to set a wrong default route than no default route. If in doubt, set the default route to the address of any known router on the local subnet.
DNS: In IPX, designed by Novell, the names (and corresponding addresses) of ALL services available on the network are stored in ALL Netware servers as a SAP table (SAP stands for Service Advertising Protocol.) Netware servers will share SAP information with each other automatically. Unfortunately, since ALL servers must know about ALL services, SAP tables can get very unwieldy on large networks, and without the benefit of advanced routing/advertising algorithms (NLSP), can flood networks with SAP broadcasts. The way IP handles name-to-address translation is called DNS. When you query your DNS server for a given name's address (such as www.novell.com), the DNS server will query one of the "root" servers for .COM. The root server tells the DNS server the address of the "authoritative" DNS server for novell.com. Your DNS server then asks the DNS server of novell.com what the address of www.novell.com is; when novell.com's DNS ponies up the address of www.novell.com, your local DNS "remembers" where www.novell.com was, so it doesn't have to look again the next time someone asks for that name's address. Note that DNS uses special records for mail routing, called MX records, that usually differ from the host addresses. Therefore, an ftp (or www, or gopher,...) connection to microsoft.com probably reaches a different address than mail sent to somebody@microsoft.com. Of course, the giveaway that you're talking mail ("MX" record) addresses, rather than host ("A" record) addresses, is the "@" in the address. Host names never have @ symbols, which is why you connect to www.microsoft.com, never www@microsoft.com.
BOOTP and DHCP: BOOTP was designed to ease the configuration of desktop IP stacks. In a nutshell, a BOOTP-enabled workstation sends out a broadcast BOOTP request, which is answered by a BOOTP server. The answer includes workstation address, subnet mask, default route, and DNS location(s). DHCP is generally accepted as the "next generation" of BOOTP. Whereas BOOTP statically assigns IP addresses by MAC address, DHCP supports address "leasing" where an address is granted to a specific MAC address for a finite amount of time, and can be reused after a specified amount of time. DHCP also supports fields beyond BOOTP, most notably returning information about the location of WINS server to Windows NT clients, and the location of DSS servers to Netware/IP clients. (A DHCP service is included with NT, and is available for free download as part of the Netware/IP upgrade for Netware 4.10 servers, see http://support.novell.com/.)
An IP Address is broken up into three parts: the network portion, the subnet portion (optional), and the host portion. The size of the network portion is determined by the first byte of the address:
| First Byte | Class | Network Mask (explained later) |
| 1-126 | "A" | 255.0.0.0 |
| 128-191 | "B" | 255.255.0.0 |
| 192-223 | "C" | 255.255.255.0 |
Note: people often refer to any subnet with a mask of 255.255.255.0 as being a class "C" network; however, the only "true" class "C" networks have a first byte in the range of 192-223. This becomes important when you start subnetting.
The Subnet portion of an IP address is actually optional, and, in fact, is
rarely used on class "C" networks. Generally, you can subnet any network you
have control over, in any valid way you want. The tricky part is understanding
what is valid.
Lets start with some ground rules:

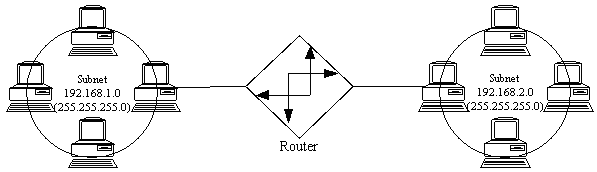
...This is invalid since the [exact] same subnet exists on both sides of the router.
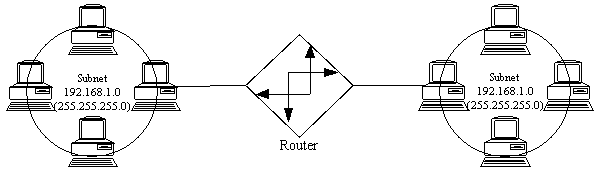
...This is invalid since the same subnet exists on both sides of the router. Watch that subnet mask! (See below.)
These
images created using SmartDraw. Click Here for a free trial copy.
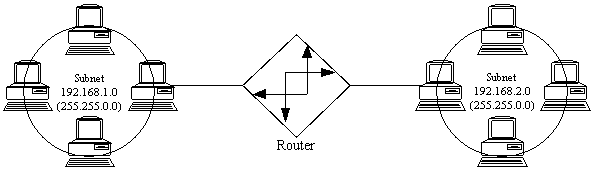
...This is invalid because a the same host address could be "valid" on either subnet, e.g. 192.168.2.100. Even though the right side subnet is valid by itself, it is actually a small piece of the left side network.
| Exception! | Address overlap of this sort is usually not allowed between two
physical subnets: unless the router was specifically configured to
"pretend" it was every address on 192.168.2.0 for its left-side interface
in the diagram, it would be impossible for hosts on one side of the router
to communicate with hosts on the other side. In this diagram, the
192.168.2.0 subnet is known as a "stub subnet"; the process of pretending
you are hosts you're not, in order to facilitate routing packets to a stub
subnet, is known as "proxy arp." No two hosts on the Internet can have the
same IP address. If you create a stub subnet, no host on the "main" side
can have an address that might be valid on the "stub" side. [Please also note that the diagram in question is talking about two physical subnets attached to one router, not routing tables on upstream routers, which would aggregate both networks into one route of 192.168.0.0/16.] |
|---|
The Glossy Explanation
When using a subnet mask of 255.255.0.0, the first two bytes indicate the network you're on, and the last two bytes indicate the host you are on that network. Very rarely will you find a network segment with 65,534 hosts on it, though. You'll only find network masking like that used closer to the Internet backbone, in the context of, "All them hosts [and subnets thereof] are thataway." Now, that brings up one of the nice features of subnet masking: you can lump a bunch of networks together by using unusual subnet masking; however, that sort of activity generally doesn't happen on the near side of the 'net.
When using a subnet mask of 255.255.255.0, the first three bytes indicate the network you're on, and the last byte is the host you are on that network. Hosts .1 through .254 are available.
By using a subnet mask of 255.255.255.128, you can split that network into two halves, the first half containing the host addresses .1 through .126, the second half containing the host addresses .129 through .254. Note that on a true class "C" network, you can't use the top subnet, since the bit in the subnet portion (one bit on a class "C") would be one (refer to ground rule "D".)
By using a subnet mask of 255.255.255.192, you can split the network into four portions, each with 64 hosts (62 usable.) Subnetwork one includes the addresses .1 through .62, subnetwork two includes the addresses .65 through .126, subnetwork three includes .129 through .190, and subnetwork four includes the hosts .193 through .254. On a true class "C" network, subnetwork four is not valid.
You can not arbitrarily cut a piece out of one network and place it on another segment; the best you can do with a given subnet (or network) is chop it in halves, or quarters, or eighths, or sixteenths... (note the "powers of two" progression; this is an effect of stealing bit positions from the host address section, and giving those bits positions to the subnet portions. It gets complicated...)
or, By The Way - Forget Everything You Just Learned, It Became Obsolete in 1995
Under RFC 1812, things have changed..!
Perhaps the most significant change on the near side of the 'net under RFC 1812 is Classless Inter-Domain Routing (CIDR, pronounced "Cider"). Under CIDR, the concept of separate "network" and "subnet" portions is now considered outdated, and is being replaced by a "classless" addressing scheme where addresses can be "subnetted" more freely, without consideration of the "class" of address. With the removal of the subnet portion, and the liberalization of (what is now called) the network prefix, there is no longer a consideration of whether or not the bits within the subnet portion are all ones; in other words, you no longer lose a subnet when you break up what used to be known as a class "C" network. You can also aggregate formerly class "C" networks together using network prefixes fewer than 24 bits long. For example, you could combine the formerly class "C" networks 192.168.2.0 and 192.168.3.0 into a single subnet with 510 usable addresses, by using a network mask of 255.255.254.0. What you're really saying here is that the last bit of the third byte now belongs to the "host number" portion of the address, and the "network prefix" is 23 bits (two bytes and seven bits) long. Therefore, the two networks being combined must be contiguous, and the third byte must be even on the lower numbered network. You could not combine, for example, 192.168.2.0 and 192.168.5.0; not could you combine 192.168.11.0 and 192.168.12.0. You could follow similar rules to combine four contiguous class "C" style networks, but the third byte of the lowest numbered network would have to be a multiple of four. This sort of thing is routinely done (on an increasingly larger scale) as you get closer to the Internet backbones.
Most of the other effects of RFC 1812 and CIDR routing affect areas of the 'net closer to the backbone, and mostly work to reduce the size (or at least the rate of growth) of routing tables in backbone routers.
A good analogy for IP addressing and packet forwarding (routing) is the snail mail analogy. Consider an IP packet to be an envelope containing data, and having an address on the front. Every TCP/IP-enabled network interface can be compared to a mailbox. Every mailbox (interface) has an IP address. The four bytes of an IP address can be compared to the state, city, street, and house number fields on the front of a snail mail envelope. A router in this analogy is a post office, that sorts and forwards mail based on the address on the envelope (packet header.) If the address is on the same street (based on the subnet mask,) the envelope (packet) is sent directly to the destination mailbox (interface) via local courier (Ethernet?). If the address is determined to be on another street, or in another city or state, the envelope (packet) is delivered via local courier (Ethernet?) to the street's post office (router), where the postal workers (routing software) sort and forward mail based on established post office sorting procedures (routing tables.) The breakdown in this analogy, of course, is that no routing software has ever been known to shoot people. (Just Kidding :-)
Now, think back to first grade math, when the teacher was describing the decimal numbering system. As it happens, it's called "decimal" (the root of the word is from Latin decima, a tenth part or tithe) because it's a numbering system that uses ten numbers: the numbers zero through nine. If you need to represent a number larger than nine, you have to start adding additional digits; then the teacher described the ones place, the tens place, the hundreds place, etc. For example, the number 45678 has a four in the "ten thousands" place, a five in the "thousands" place, a six in the "hundreds" place, a seven in the "tens" place, and a 8 in the "ones" place:
| Ten Thousands | Thousands | Hundreds | Tens | Ones |
| 4 | 5 | 6 | 7 | 8 |
| (Binary Places, expressed as Decimal:) | 32768 | 16384 | 8192 | 4096 | 2048 | 1024 | 512 | 256 | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| 1 | 0 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 1 | 1 | 0 |
| Decimal | Binary | Decimal | Binary | Decimal | Binary | Decimal | Binary | |||
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 1 | 11 | 1011 | 21 | 10101 | 31 | 11111 | |||
| 2 | 10 | 12 | 1100 | 22 | 10110 | 32 | 100000 | |||
| 3 | 11 | 13 | 1101 | 23 | 10111 | 33 | 100001 | |||
| 4 | 100 | 14 | 1110 | 24 | 11000 | 34 | 100010 | |||
| 5 | 101 | 15 | 1111 | 25 | 11001 | 35 | 100011 | |||
| 6 | 110 | 16 | 10000 | 26 | 11010 | 36 | 100100 | |||
| 7 | 111 | 17 | 10001 | 27 | 11011 | 37 | 100101 | |||
| 8 | 1000 | 18 | 10010 | 28 | 11100 | 38 | 100110 | |||
| 9 | 1001 | 19 | 10011 | 29 | 11101 | 39 | 100111 | |||
| 10 | 1010 | 20 | 10100 | 30 | 11110 | 40 | 101000 |
| Class | Network bits | Network Mask | Network Mask (binary) |
|---|---|---|---|
| A | 8 | 255.0.0.0 | b11111111.00000000.00000000.00000000 |
| B | 16 | 255.255.0.0 | b11111111.11111111.00000000.00000000 |
| C | 24 | 255.255.255.0 | b11111111.11111111.11111111.00000000 |
| Operation | Result | Examples |
|---|---|---|
| AND | true if A AND B are true | 1 AND 1 = 1 1 AND 0 = 0 0 AND 1 = 0 0 AND 0 = 0 |
| OR | true if A OR B are true | 1 OR 1 = 1 1 OR 0 = 1 0 OR 1 = 1 0 OR 0 = 0 |
| XOR (eXclusive Or) | true if either A or B are true | 1 XOR 1 = 0 1 XOR 0 = 1 0 XOR 1 = 1 0 XOR 0 = 0 |
| NOT | opposite of A | NOT 1 = 0 NOT 0 = 1 |
| Networks | Networks, in Binary |
|---|---|
| 192.168.8.0 | b11000000.10101000.00001000.00000000 |
| 192.168.9.0 | b11000000.10101000.00001001.00000000 |
| 192.168.10.0 | b11000000.10101000.00001010.00000000 |
| 192.168.11.0 | b11000000.10101000.00001011.00000000 |
| Mask, 255.255.252.0 | b11111111.11111111.11111100.00000000 |
| Networks | Networks, in Binary |
|---|---|
| 192.168.10.0 | b11000000.10101000.00001010.00000000 |
| 192.168.11.0 | b11000000.10101000.00001011.00000000 |
| 192.168.12.0 | b11000000.10101000.00001100.00000000 |
| 192.168.13.0 | b11000000.10101000.00001101.00000000 |
| Mask, 255.255.252.0 | b11111111.11111111.11111100.00000000 |
Ever get one of those spam e-mails where the IP address is an integer? Type it in here and it will be decoded: Excercises:
- Enter your IP address and your default router's IP address. Are you on the same subnetwork?
- Compare your IP address and the IP address of your DNS server(s). Are you on the same network as your DNS server(s)?
- Remember, this principle is used for routing, too. Watch what happens when you increment and decrement the number of bits in the subnet mask (use the arrow buttons).
- If your ISP has assigned your organization multiple contiguous subnets, see if you can determine the network prefix they use for routing to you by entering the top and bottom IP addresses you own, then widening the network mask until they are on the same subnet!
I've also noticed a freeware Win32 app that does similar things at http://www.net3group.com/ipcalc.html-ssi.
Before: Network 192.168.1.0:
After: Split into three parts using a subnet mask of 255.255.255.192
These
images created using SmartDraw. Click Here for a free trial copy.
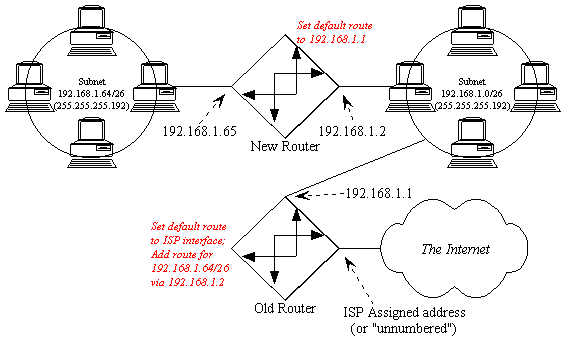
What we need to do now is tell the router what happened...
First, you have to tell the old router that the network attached to its Ethernet interface has changed (specifically, the network mask has changed, and often, the address of the Ethernet interface has changed.) If you were adding a new subnet, rather than splitting an existing one, then you could probably skip this step.
Second, you have to tell the old router where to find the new network (what the next hop is.) A typical command would look something like this:
ROUTE 192.168.1.64/255.255.255.192 192.168.1.2
What you're telling the old router with that statement is, "if you need to route packets to the subnetwork that starts at 192.168.1.64 and has a subnet mask of 255.255.255.192, you should forward all packets intended for that network to the router at 192.168.1.2."
Third, be sure the default route for the new router is set to 192.168.1.1.
Note that the automatic routing protocol (IP) RIP does not understand subnet masking. If you are using protocols that do, such as OSPF or EIGRP, then you probably aren't reading this document. Actually using routing protocols tends to be irrelevant on the "near side" of the net, since there is generally only one path to the Internet from any given workstation on a LAN. Multiple routes tend to be a problem only closer to the backbone, and that's your ISP's problem.
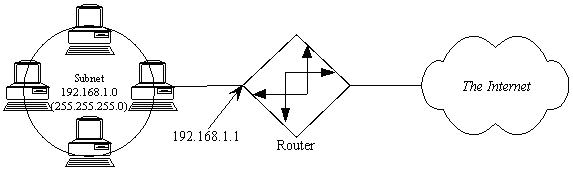
Step #1: Determine if the IP stack is alive. There is a reserved address 127.0.0.1 called "localhost". A successful ping to 127.0.0.1 means your IP stack is working properly. A ping to localhost doesn't even make it on the wire.
Step #2: Determine if you can talk onto the wire. Ping yourself. If your address is 192.168.1.1, then ping 192.168.1.1. Actually, the packet may or may not actually make it on the wire, depending on your implementation. But it doesn't hurt.
Step #3: See if you can ping anyone else. Ping your default router. Make sure your default router is on your same subnet! The easy way to do this is to refer to the "glossy explanation" of subnetting in Section 4, and to make sure both addresses can exist in the same subnet. If you can't ping your default router, either the router is down (easily checked from another workstation) or there's something wrong at your workstation. Make sure your workstation has the subnet mask set correctly, and that you and the router are using the same frame type. The default frame type for TCP/IP is Ethernet_II on Ethernet LANs, and TOKEN-RING_SNAP on Token-Ring LANs. Cisco routers refer to Ethernet_II as encapsulation type ARPA.
Step #4: See if you ping the far interface of the default router. All routers have more than one interface (or they wouldn't be routers, right?) If you know the interface of the far side of the router, ping that. That verifies that your default route is set properly. If you don't know the address of another router interface, skip to step 5.
Step #5: Ping the address of your name server. Your name server address is given to you by your ISP. If you cannot ping your name server, try to trace your route to it. The UNIX version of the command is "traceroute"; Windows renamed it to "tracert". (In related news, Jason D. has informed me that the traceroute command for OS/2 is "tracerte".) An example:
D:\WINDOWS>tracert ns.orbis.net Tracing route to ns.orbis.net [205.164.72.2] over a maximum of 30 hops: 1 1 ms 1 ms 1 ms 192.168.1.254 2 60 ms 61 ms 64 ms 205.164.75.1 3 64 ms 62 ms 65 ms tamino.summit-ops.orbis.net [205.164.72.129] 4 78 ms 77 ms 78 ms ns.orbis.net [205.164.72.2] Trace complete. D:\WINDOWS> |
Note: if you actually get names, you not only have verified Internet connectivity, but you also know your DNS is properly set up. Congratulations! You are on the Internet. If you have problems at this point, it's time to call your ISP.
Step #6: If you didn't get any names in your route trace, don't panic: Try to ping www.novell.com or www.microsoft.com. If you can ping, by name, either of those addresses, you are set up for Internet access. If you get a message like, "Unable to resolve novell.com" then you need to make sure your DNS is set up properly. If you get a "host unreachable" then you probably are set up OK but the 'net is just a bit congested. (Or you haven't set your workstation's default route properly.)
Typically, I start with step #6, and if that fails, go to step #1.
*Second most useful? Probably the most useful tool for diagnosing connection
problems across the Internet is traceroute (or tracert for Windows users.) My
absolute favorite utility, and the first program I run when I'm having a
problem, is Ping Plotter, which is a GUI traceroute tool that shows graphically
the time to each hop along the way to a destination:
Ping Plotter is
available at http://www.pingplotter.com/ Both
"freeware" and registered ($15) versions are available. And if you end up using
it more than once or twice a week, do the Right Thing and register it. It's a
more than reasonable price, and maybe then Pete will release enhanced versions
on a more regular basis :-)
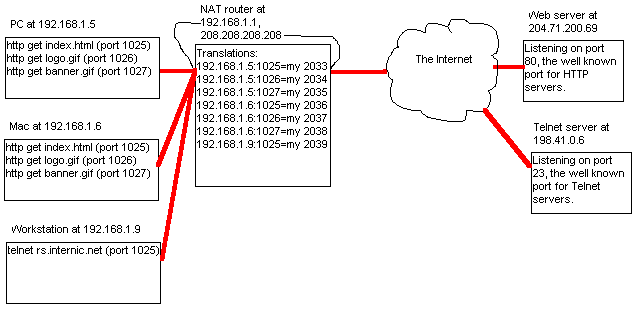
Every TCP (or UDP) communication has a source port and destination port number in the TCP (or UDP) header. Every TCP/IP communication can be uniquely identified as [Source IP]:[Source Port] <---> [Dest. IP]:[Dest Port]. This is how a Web browser can load several images at once and keep track of which packet is for which image. The source port is different for each TCP image-download connection, though the destination port is 80 in each case. For example:
| Source IP | Source Port | Dest IP | Dest Port | Notes |
| 192.168.1.1 | 1025 | 10.101.10.1 | 80 | index.html |
| 192.168.1.1 | 1026 | 10.101.10.1 | 80 | logo.gif |
| 192.168.1.1 | 1027 | 10.101.10.1 | 80 | backgrnd.gif |
Note that each file getting downloaded has a different source port number; this is how the communications are differentiated (this packet is part of logo.gif, this packet is part of index.html, etc). Now, let's assume that index.html is finished, but the graphics are loading slowly. While the user is waiting, he/she decides to open a telnet session to rs.internic.net. The table of open sessions would look like this:
| Source IP | Source Port | Dest IP | Dest Port | Notes |
| 192.168.1.1 | 1026 | 10.101.10.1 | 80 | logo.gif |
| 192.168.1.1 | 1027 | 10.101.10.1 | 80 | backgrnd.gif |
| 192.168.1.1 | 1028 | 198.41.0.9 | 23 | telnet rs.internic.net |
Now, I could go into exhaustive detail on how a TCP connection is set up and torn down, flow is controlled, and dropped packets are resent. Instead, I'll just say that TCP connections are set up and torn down, and there is flow control and automatic dropped packet redelivery. TCP is like certified mail; if no return receipt is gotten, the packet is resent (I'm oversimplifying but it's close enough.) TCP is used for "reliable" communications, where all data must get through, and must get there in the correct order.
A UDP packet, on the other hand, is more like junk mail. No effort is expended to make sure it arrives at the destination, or that all packets arrived that were sent. UDP is generally used for real-time applications like Internet radio and online gaming, where dropped packets need not be resent, and would probably be old if they were. UDP is also used when upper-layer protocols do their own flow control and data stream checking and correcting, as is the case in NCP/IP (Netware/IP) and SMB/IP (Microsoft Networking).
Web, Telnet, Mail, and other servers "listen" for new communications at "well-known" TCP port numbers. A short list:
| Service | "Well-Known" Port Number |
| FTP | 21&20 (don't ask) |
| Telnet | 23 |
| SMTP Mail | 25 |
| HTTP (Web) | 80 |
| POP3 Mail | 110 |
| News | 119 |
| IRC | 6667 |
| QuakeWorld :-) | 27500 |
Publicly available services are generally always reached by connecting to their well-known port numbers.
A more complete list of assigned Well-Known Ports can be found at http://www.isi.edu/in-notes/iana/assignments/port-numbers
A
list of common vulnerabilities by port can be found at http://www.networkice.com/advice/Exploits/Ports/.
Incidentally, the maintainers of this list produce a "personal firewall" product
for Windows systems called BlackICE Defender http://www.networkice.com/html/blackice_defender.html
that I use and recommend highly for servers. For personal use, look at ZoneAlarm
(http://www.zonealarm.com/), which is
effective bidirectionally, but requires too much user intervention to be used
for servers in a lights-out environment. And you can't beat the price.
:-)
(Thanks to B.B. for noticing the broken links and suggesting these new
ones..!)
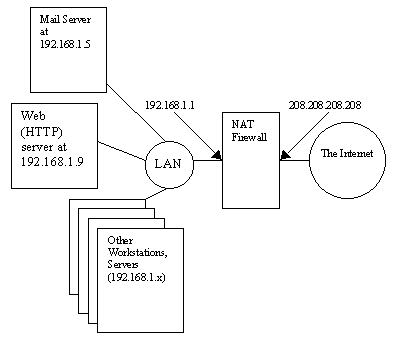
| "Listening" Port | "Internal" Address |
|---|---|
| 208.208.208.208:25 | 192.168.1.5:25 |
| 208.208.208.208:80 | 192.168.1.9:80 |
Let's start with an example: If you ask your local name server for the address of "www.north-america.example.com" the name server will do the following:
1. Check to see if it already knows the address of
"www.north-america.example.com" (let's assume it doesn't. The example is more
interesting that way.)
2. The DNS server queries a "root" server for the
address of "www.north-america.example.com". All fully-functional DNS servers are
configured with a static list of root servers, available at ftp://ftp.rs.internic.net/domain/named.root.
3.
The root server will refer your DNS to a list of ".com" servers.
4. Your DNS
will query one of the ".com" servers for the address of
"www.north-america.example.com"
5. The ".com" name server queried refers your
name server to a list of name servers for "example.com".
6. Your DNS server
then asks one of the "example.com" name servers for the address of
"www.north-america.example.com".
7. One of two things can happen here. If the
"example.com" name server queried knows the address of
"www.north-america.example.com" then it returns that address to your DNS server.
If the "north-america" subdomain has been delegated to some other name
server(s), then that name server list (of name servers that service the zone,
"north-america.example.com") will be returned to your DNS, and your DNS will
query one of those servers for the address of "www.north-america.example.com".
Note that your DNS remembers, or caches, all the information it retrieves this way. Therefore, if you asked your local DNS for the address of "ftp.north-america.example.com", then it would directly ask the name server finally referenced in step 7 (above) for the address of "ftp.north-america.example.com". This prevents the top-level and root servers from being more heavily loaded than they already are. (It's also interesting to note that the root servers are also the top-level domain servers for the US domains.) It is possible to set up a caching-only DNS server that processes and caches requests, but isn't directly knowledgeable ("authoritative") about any domains itself.
Domains, Zones, and Authority
There are several different types of name servers. There is one Primary name server for each domain or delegated subdomain ("zone"). A "zone" refers to the domain and subdomain(s) (if any) a server is authoritative for. In many cases "zone" and "domain" mean the same thing, but when you start delegating authority for subdomains, they get their own zone to administer, although it's part of your domain. For example, the root servers are authoritative for the ".com" zone but they aren't authoritative for the entire ".com" domain. "example.com" is, in fact, a subdomain of the ".com" domain, but is a different DNS zone. Zone boundaries typically follow administrative control boundaries: since the people managing the ".com" domain are not the same as the people managing the "example.com" domain, a new zone is created and authority for the zone is delegated to that zone's name servers.
Every Primary name server should have at least one Secondary name server. A Secondary name server simply copies the zone information from the zone's Primary server. Secondary name servers also answer DNS requests authoritatively. It is strongly suggested that at least one secondary name server be on another physical network. If someone wants to send you mail, and your mail server is unreachable, the mail is queued and retried, but eventually delivered. If the sending mail server is told there is no mail server or host information about your network (which is what happens if all authoritative DNSes are unreachable) then the mail bounces.
If you set up a Primary name server, it is necessary to have the parent domain delegate authority for your zone to you. For example, if you wanted to be the authoritative name server for the domain "reallyslow.net", you would have to ask the administrators for ".net" (InterNIC, in this case) to delegate the zone authority for "reallyslow.net" to you. Similarly, if the engineering department wanted to run there own name server for "engineering.reallyslow.net", then they would have to ask you to delegate the zone "engineering.reallyslow.net" to their name server(s).
It is usually possible to look up an address and come up with a machine name. This is called a "reverse lookup," because instead of getting an address from a name, you are getting a name from an address. The reverse lookup system behaves very similarly to "normal" DNS; in fact, you could almost consider it to be a parallel DNS system. Lookup is done in reverse order by octet with the domain "in-addr.arpa" appended. Let's say you "own" a network 192.168.45.0 with a subnet mask of 255.255.255.0. You would contact the administrator for "168.192.in-addr.arpa" and ask him/her to delegate the authority for the zone "45.168.192.in-addr.arpa" to your name server. On your name server you would create a zone file for reverse lookups that would be authoritative for that zone.
Types of DNS Records
SOA: A Start of Authority record is used at the top of every zone file to
indicate the zone that the file is authoritative for. The SOA record also
contains administrative contact information, the serial number for the file
(which must be incremented whenever the file is updated), and various default
timeout and retry values for the domain.
reallyslow.net. IN SOA turtle.reallyslow.net root.reallyslow.net ([various numbers])
A: Address records actually provide name-to-address mapping:
turtle.reallyslow.net. IN A 192.168.45.10 caterpillar.reallyslow.net. IN A 192.168.45.12
CNAME: Canonical name records are "alias" records that are often used to map
conventional names like "www.reallyslow.net" to the actual name ("A" record) of
the computer providing World Wide Web services for the domain. Other names use
by convention include "ftp." for ftp services, "mail." for e-mail servers, and
"ns" for name servers.
www.reallyslow.net. IN CNAME turtle.reallyslow.net. snail.reallyslow.net. IN CNAME caterpillar.reallyslow.net.
NS: Name Server records indicate which machines are used as name servers. NS
records sometimes point to host names ("A" records), sometimes point to aliases
("CNAME" records), and sometimes just list an IP address.
reallyslow.net. IN NS turtle.reallyslow.net. reallyslow.net. IN NS snail.reallyslow.net.
MX: Mail eXchanger records indicate which machines are mail servers for a
domain and what their preference is. The lower the number, the higher the
preference (hey, I didn't invent it.) Other mail servers will try to send mail
to the highest preference mail server first. We want email for
anyone@reallyslow.net to be delivered to the machine mail.reallyslow.net:
reallyslow.net IN MX 10 mail.reallyslow.net.or, if you used another company to handle your email services...
reallyslow.net IN MX 10 mail.notquitesoslow.net.MX records should not point to CNAME records.
PTR: Reverse lookup pointers are used by the reverse lookup system to map
addresses to names (notice the reversed order of the octets:)
10.45.168.192.in-addr.arpa. IN PTR turtle.reallyslow.net. 12.45.168.192.in-addr.arpa. IN PTR caterpillar.reallyslow.net.
Note that host names never include "@" symbols. An "@" symbol almost always indicates an email address [one notable exception being a message identifier for a Usenet newsgroup posting. Tks again B.B.] The name to the right of the "@" sign is queried for an MX record and mail is delivered to the machine indicated by the MX record(s). In a DNS file, the "@" symbol is a placeholder used to represent "the current domain" as it was named in named.boot. named.boot is the standard file name used by DNS ("named", pronounced "name dee") servers. A basic named.boot looks like this:
primary reallyslow.net db.reallyslow.net primary 0.0.127.IN-ADDR.ARPA db.127.0.0 primary 45.168.192.in-addr.arpa db.inaddrWe're telling BIND that it is authoritative for the "standard" zone "reallyslow.net", and also primary for the reverse lookup zones for the subnets 192.168.45.x and 127.0.0.x. (The only entry for 127.0.0.x is 127.0.0.1, which maps to LOCALHOST, which is a reserved address and name for "this machine". In other words, you will always have a VERY fast ping to localhost :-) The zone file for 45.168.192.in-addr.arpa contains standard PTR records after the SOA record. Note that it's really easy to forget to update named.boot if you add a new domain to your name server (hint, hint.)
If you are going to set up your own name server, I highly recommend the book DNS and BIND by Paul Albitz and Cricket Liu (O'Reilly & Associates, ISBN 1-56592-010-4). On the 'net, check out the "BIND Operations Guide" in Windows Write format at ftp://ftp.software.com/BIND-NT/BOG.wri.
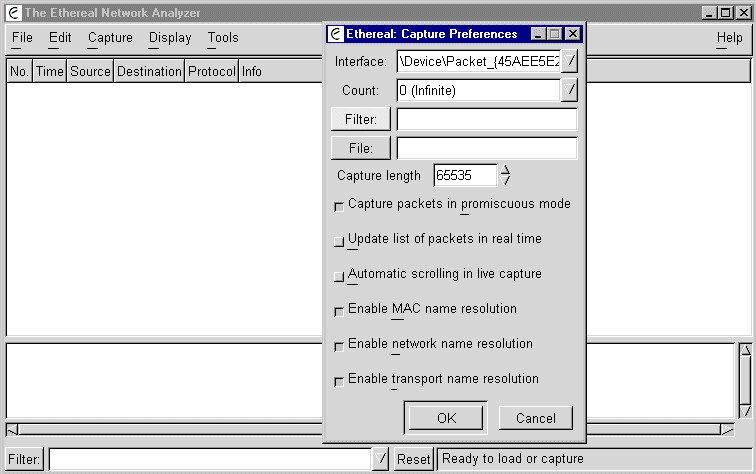
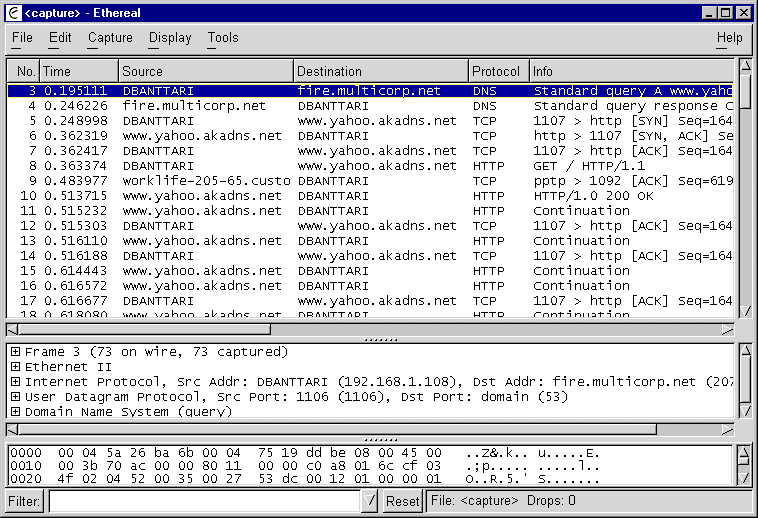
Frame 10 (62 on wire, 62 captured)
Ethernet II
Destination: 00:30:94:d3:11:54 (mkc-65-26-66-1.kc.rr.com)
Source: 00:04:75:19:dd:be (00:04:75:19:dd:be)
Type: IP (0x0800)
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: kscymo1-mls1.rdc-kc.rr.com (24.94.163.165)
User Datagram Protocol, Src Port: 1075 (1075), Dst Port: domain (53)
Domain Name System (query)
Transaction ID: 0x000d
Flags: 0x0100 (Standard query)
Questions: 1
Answer RRs: 0
Authority RRs: 0
Additional RRs: 0
Queries
www.yahoo.com: type A, class inet
|
Frame 13 (62 on wire, 62 captured)
Ethernet II
Destination: 00:04:75:19:dd:be (00:04:75:19:dd:be)
Source: 00:30:94:d3:11:54 (mkc-65-26-66-1.kc.rr.com)
Type: IP (0x0800)
Internet Protocol, Src Addr: kscymo1-mls1.rdc-kc.rr.com (24.94.163.165), Dst Addr: DBANTTARI (65.28.72.130)
User Datagram Protocol, Src Port: domain (53), Dst Port: 1077 (1077)
Domain Name System (response)
Transaction ID: 0x0009
Flags: 0x8180 (Standard query response, No error)
Questions: 1
Answer RRs: 13
Authority RRs: 8
Additional RRs: 7
Queries
www.yahoo.com: type A, class inet
Name: www.yahoo.com
Type: Host address
Class: inet
Answers
www.yahoo.com: type CNAME, class inet, cname www.yahoo.akadns.net
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.223
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.228
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.224
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.177
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.178
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.222
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.225
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.229
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.179
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.176
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.226
www.yahoo.akadns.net: type A, class inet, addr 64.58.76.227
Authoritative nameservers
akadns.net: type NS, class inet, ns ZA.akadns.net
akadns.net: type NS, class inet, ns ZB.akadns.net
akadns.net: type NS, class inet, ns ZC.akadns.net
akadns.net: type NS, class inet, ns ZD.akadns.net
akadns.net: type NS, class inet, ns ZE.akadns.net
akadns.net: type NS, class inet, ns ZF.akadns.net
akadns.net: type NS, class inet, ns ZG.akadns.net
akadns.net: type NS, class inet, ns ZH.akadns.net
Additional records
ZA.akadns.net: type A, class inet, addr 216.32.65.105
ZB.akadns.net: type A, class inet, addr 216.200.14.118
ZC.akadns.net: type A, class inet, addr 204.178.107.227
ZD.akadns.net: type A, class inet, addr 206.132.160.36
ZE.akadns.net: type A, class inet, addr 12.47.217.11
ZF.akadns.net: type A, class inet, addr 63.215.198.79
ZG.akadns.net: type A, class inet, addr 204.248.36.131
|
Frame 14 (62 on wire, 62 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525356, Ack: 0
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525356
Header length: 28 bytes
Flags: 0x0002 (SYN)
Window size: 16384
Checksum: 0x1f12 (correct)
Options: (8 bytes)
Maximum segment size: 1360 bytes
NOP
NOP
SACK permitted
|
Frame 16 (60 on wire, 60 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906338462, Ack: 1166525357
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906338462
Acknowledgement number: 1166525357
Header length: 24 bytes
Flags: 0x0012 (SYN, ACK)
Window size: 17680
Checksum: 0x57f0 (correct)
Options: (4 bytes)
Maximum segment size: 1460 bytes
|
Frame 17 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525357, Ack: 906338463
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525357
Acknowledgement number: 906338463
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x6fad)
Frame 18 (329 on wire, 329 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525357, Ack: 906338463
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525357
Next sequence number: 1166525632
Acknowledgement number: 906338463
Header length: 20 bytes
Flags: 0x0018 (PSH, ACK)
Window size: 17680
Checksum: 0x17e5 (incorrect, should be 0x4547)
Hypertext Transfer Protocol
GET / HTTP/1.1\r\n
Accept: */*\r\n
Referer: http://www.ipprimer.com/packets.cfm\r\n
Accept-Language: en-us\r\n
Accept-Encoding: gzip, deflate\r\n
User-Agent: Mozilla/4.0 (compatible; MSIE 5.5; Windows NT 5.0)\r\n
Host: www.yahoo.com\r\n
Connection: Keep-Alive\r\n
Cookie: B=shyg4f0xg4tmp&b=2&f=v\r\n
\r\n
|
Frame 20 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906338463, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906338463
Next sequence number: 906339823
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x4df8 (correct)
Hypertext Transfer Protocol
HTTP/1.0 200 OK\r\n
Date: Sun, 14 Oct 2001 03:53:44 GMT\r\n
Vary: User-Agent\r\n
Connection: close\r\n
Content-Type: text/html\r\n
\r\n
Data (1242 bytes)
0000 3c 68 74 6d 6c 3e 3c 68 65 61 64 3e 3c 74 69 74 <html><head><tit
0010 6c 65 3e 59 61 68 6f 6f 21 3c 2f 74 69 74 6c 65 le>Yahoo!</title
(blah, blah, blah...)
04c0 3d 79 61 68 6f 6f 66 5f 31 34 25 32 36 73 6f 75 =yahoof_14%26sou
04d0 72 63 65 49 44 3d 79 61 68 6f rceID=yaho
Frame 21 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906339823, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906339823
Next sequence number: 906341183
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x9248 (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 6f 66 5f 31 34 22 20 74 61 72 67 65 74 3d 22 5f of_14" target="_
0010 74 6f 70 22 3e 3c 69 6d 67 20 77 69 64 74 68 3d top"><img width=
(blah, blah, blah...)
0530 38 33 3b 0a 3c 61 20 68 72 65 66 3d 72 2f 67 63 83;.<a href=r/gc
0540 3e 47 65 6f 43 69 74 69 65 73 3c 2f 61 3e 20 26 >GeoCities</a> &
|
Frame 22 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906341183
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906341183
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x63fa)
Frame 23 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906341183, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906341183
Next sequence number: 906342543
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x59c0 (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 23 31 38 33 3b 0a 3c 61 20 68 72 65 66 3d 72 2f #183;.<a href=r/
0010 67 72 3e 47 72 65 65 74 69 6e 67 73 3c 2f 61 3e gr>Greetings</a>
(blah, blah, blah...)
0530 3b 20 3c 61 20 68 72 65 66 3d 73 2f 32 30 38 35 ; <a href=s/2085
0540 3e 4d 69 63 68 61 65 6c 20 4a 6f 72 64 61 6e 3c >Michael Jordan<
Frame 24 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906342543
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906342543
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x5eaa)
Frame 25 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906342543, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906342543
Next sequence number: 906343903
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x49e9 (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 2f 61 3e 3c 62 72 3e 0a 26 6e 62 73 70 3b 20 26 /a><br>. &
0010 23 31 38 33 3b 20 3c 61 20 68 72 65 66 3d 73 2f #183; <a href=s/
(blah, blah, blah...)
0530 70 61 64 64 69 6e 67 3d 34 3e 3c 74 72 3e 3c 74 padding=4><tr><t
0540 64 20 76 61 6c 69 67 6e 3d 74 6f 70 20 6e 6f 77 d valign=top now
Frame 26 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906343903, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906343903
Next sequence number: 906345263
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x7d26 (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 72 61 70 3e 3c 73 6d 61 6c 6c 3e 3c 66 6f 6e 74 rap><small><font
0010 20 73 69 7a 65 3d 33 20 66 61 63 65 3d 61 72 69 size=3 face=ari
(blah, blah, blah...)
0530 6c 6c 20 43 6f 76 65 72 61 67 65 3c 2f 61 3e 2c ll Coverage</a>,
0540 0a 3c 61 20 68 72 65 66 3d 72 2f 6e 77 3e 4e 65 .<a href=r/nw>Ne
Frame 27 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906345263
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906345263
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x540a)
Frame 28 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906345263, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906345263
Next sequence number: 906346623
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x8e4b (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 77 73 70 61 70 65 72 73 3c 2f 61 3e 2c 0a 3c 61 wspapers</a>,.<a
0010 20 68 72 65 66 3d 72 2f 74 76 3e 54 56 3c 2f 61 href=r/tv>TV</a
(blah, blah, blah...)
0530 30 33 30 33 31 36 32 34 2b 68 74 74 70 3a 2f 2f 03031624+http://
0540 75 73 2e 72 6d 69 2e 79 61 68 6f 6f 2e 63 6f 6d us.rmi.yahoo.com
Frame 29 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906346623
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906346623
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x4eba)
Frame 30 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906346623, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906346623
Next sequence number: 906347983
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0xf66f (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 2f 72 6d 69 2f 68 74 74 70 3a 2f 2f 77 77 77 2e /rmi/http://www.
0010 63 6f 6d 70 61 71 2e 63 6f 6d 2f 72 6d 69 2d 66 compaq.com/rmi-f
0020 72 61 6d 65 64 2d 75 72 6c 2f 68 74 74 70 3a 2f ramed-url/http:/
0030 2f 77 77 77 2e 63 6f 6d 70 61 71 2e 63 6f 6d 2f /www.compaq.com/
0040 79 61 68 6f 6f 2f 22 3e 3c 69 6d 67 20 73 72 63 yahoo/"><img src
0050 3d 22 68 74 74 70 3a 2f 2f 75 73 2e 61 31 2e 79 ="http://us.a1.y
0060 69 6d 67 2e 63 6f 6d 2f 75 73 2e 79 69 6d 67 2e img.com/us.yimg.
0070 63 6f 6d 2f 61 2f 63 6f 2f 63 6f 6d 70 61 71 5f com/a/co/compaq_
0080 63 6f 6d 70 5f 63 6f 72 70 2f 70 6f 77 65 72 65 comp_corp/powere
0090 64 5f 62 79 5f 77 68 69 74 65 5f 39 35 78 33 30 d_by_white_95x30
00a0 2e 67 69 66 22 20 61 6c 74 3d 22 22 20 62 6f 72 .gif" alt="" bor
00b0 64 65 72 3d 22 30 22 20 77 69 64 74 68 3d 22 39 der="0" width="9
00c0 35 22 20 68 65 69 67 68 74 3d 22 33 30 22 3e 3c 5" height="30"><
(blah, blah, blah...)
0530 61 72 63 68 3c 2f 61 3e 3c 2f 73 6d 61 6c 6c 3e arch</a></small>
0540 3c 2f 74 64 3e 3c 2f 74 72 3e 3c 74 72 3e 3c 74 </td></tr><tr><t
|
Frame 31 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906347983, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906347983
Next sequence number: 906349343
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0xc485 (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 64 20 76 61 6c 69 67 6e 3d 74 6f 70 3e 3c 62 3e d valign=top><b>
0010 26 6e 62 73 70 3b 26 23 31 38 33 3b 26 6e 62 73 ·&nbs
(blah, blah, blah...)
0530 62 6f 72 64 65 72 3d 30 3e 3c 74 72 3e 3c 74 64 border=0><tr><td
0540 20 76 61 6c 69 67 6e 3d 74 6f 70 3e 3c 62 3e 26 valign=top><b>&
Frame 32 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906349343
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906349343
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x441a)
|
Frame 33 (74 on wire, 74 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: kscymo1-mls1.rdc-kc.rr.com (24.94.163.165)
User Datagram Protocol, Src Port: 1079 (1079), Dst Port: domain (53)
Domain Name System (query)
Transaction ID: 0x000a
Flags: 0x0100 (Standard query)
Questions: 1
Answer RRs: 0
Authority RRs: 0
Additional RRs: 0
Queries
us.a1.yimg.com: type A, class inet
Frame 34 (434 on wire, 434 captured)
Ethernet II
Internet Protocol, Src Addr: kscymo1-mls1.rdc-kc.rr.com (24.94.163.165), Dst Addr: DBANTTARI (65.28.72.130)
User Datagram Protocol, Src Port: domain (53), Dst Port: 1079 (1079)
Domain Name System (response)
Transaction ID: 0x000a
Flags: 0x8180 (Standard query response, No error)
Questions: 1
Answer RRs: 3
Authority RRs: 9
Additional RRs: 9
Queries
us.a1.yimg.com: type A, class inet
Name: us.a1.yimg.com
Type: Host address
Class: inet
Answers
us.a1.yimg.com: type CNAME, class inet, cname a32.g.a.yimg.com
a32.g.a.yimg.com: type A, class inet, addr 24.94.162.91
a32.g.a.yimg.com: type A, class inet, addr 24.94.162.90
Authoritative nameservers
g.a.yimg.com: type NS, class inet, ns n0g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n1g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n6g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n2g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n3g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n7g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n4g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n5g.a.yimg.com
g.a.yimg.com: type NS, class inet, ns n8g.a.yimg.com
Additional records
n0g.a.yimg.com: type A, class inet, addr 24.94.162.85
n1g.a.yimg.com: type A, class inet, addr 24.94.162.86
n6g.a.yimg.com: type A, class inet, addr 164.113.247.89
n2g.a.yimg.com: type A, class inet, addr 24.94.162.85
n3g.a.yimg.com: type A, class inet, addr 24.94.162.85
n7g.a.yimg.com: type A, class inet, addr 18.7.20.66
n4g.a.yimg.com: type A, class inet, addr 24.94.162.85
n5g.a.yimg.com: type A, class inet, addr 24.94.162.85
n8g.a.yimg.com: type A, class inet, addr 24.94.162.85
|
Frame 35 (62 on wire, 62 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: a32.g.a.yimg.com (24.94.162.91)
Transmission Control Protocol, Src Port: 1080 (1080), Dst Port: http (80), Seq: 1166630283, Ack: 0
Source port: 1080 (1080)
Destination port: http (80)
Sequence number: 1166630283
Header length: 28 bytes
Flags: 0x0002 (SYN)
Window size: 16384
Checksum: 0x578f (correct)
Options: (8 bytes)
Maximum segment size: 1360 bytes
NOP
NOP
SACK permitted
Frame 36 (62 on wire, 62 captured)
Ethernet II
Internet Protocol, Src Addr: a32.g.a.yimg.com (24.94.162.91), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1080 (1080), Seq: 3443607970, Ack: 1166630284
Source port: http (80)
Destination port: 1080 (1080)
Sequence number: 3443607970
Acknowledgement number: 1166630284
Header length: 28 bytes
Flags: 0x0012 (SYN, ACK)
Window size: 32640
Checksum: 0x011a (correct)
Options: (8 bytes)
Maximum segment size: 1360 bytes
NOP
NOP
SACK permitted
Frame 37 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: a32.g.a.yimg.com (24.94.162.91)
Transmission Control Protocol, Src Port: 1080 (1080), Dst Port: http (80), Seq: 1166630284, Ack: 3443607971
Source port: 1080 (1080)
Destination port: http (80)
Sequence number: 1166630284
Acknowledgement number: 3443607971
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x4472 (incorrect, should be 0x67ea)
Frame 38 (318 on wire, 318 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: a32.g.a.yimg.com (24.94.162.91)
Transmission Control Protocol, Src Port: 1080 (1080), Dst Port: http (80), Seq: 1166630284, Ack: 3443607971
Source port: 1080 (1080)
Destination port: http (80)
Sequence number: 1166630284
Next sequence number: 1166630548
Acknowledgement number: 3443607971
Header length: 20 bytes
Flags: 0x0018 (PSH, ACK)
Window size: 17680
Checksum: 0x457a (incorrect, should be 0x59d2)
Socks Protocol
|
Frame 39 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906349343, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906349343
Next sequence number: 906350703
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0xce3d (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 6e 62 73 70 3b 26 23 31 38 33 3b 26 6e 62 73 70 nbsp;· 
0010 3b 3c 2f 62 3e 3c 2f 74 64 3e 3c 74 64 20 77 69 ;</b></td><td wi
(blah, blah, blah...)
0530 6f 72 6b 79 20 52 6f 6d 61 6e 6f 3c 2f 61 3e 2c orky Romano</a>,
0540 20 3c 61 20 68 72 65 66 3d 73 2f 32 31 38 39 3e <a href=s/2189>
Frame 40 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906350703
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906350703
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x3eca)
Frame 41 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906350703, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906350703
Next sequence number: 906352063
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x4b3c (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 54 72 61 69 6e 69 6e 67 20 44 61 79 3c 2f 61 3e Training Day</a>
0010 3c 2f 73 6d 61 6c 6c 3e 3c 2f 74 64 3e 3c 2f 74 </small></td></t
(blah, blah, blah...)
0530 0a 3c 61 20 68 72 65 66 3d 72 2f 61 74 3e 41 74 .<a href=r/at>At
0540 6c 61 6e 74 61 3c 2f 61 3e 20 2d 0a 3c 61 20 68 lanta</a> -.<a h
Frame 42 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906352063, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906352063
Next sequence number: 906353423
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0xa86d (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 72 65 66 3d 72 2f 62 6f 3e 42 6f 73 74 6f 6e 3c ref=r/bo>Boston<
0010 2f 61 3e 20 2d 0a 3c 61 20 68 72 65 66 3d 72 2f /a> -.<a href=r/
(blah, blah, blah...)
0530 65 64 73 3c 2f 61 3e 20 2d 0a 3c 61 20 68 72 65 eds</a> -.<a hre
0540 66 3d 72 2f 6c 65 3e 45 76 65 6e 74 73 3c 2f 61 f=r/le>Events</a
Frame 43 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906353423
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906353423
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x342a)
Frame 44 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906353423, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906353423
Next sequence number: 906354783
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x8df1 (correct)
Hypertext Transfer Protocol
Data (1360 bytes)
0000 3e 20 2d 0a 3c 61 20 68 72 65 66 3d 72 2f 6c 64 > -.<a href=r/ld
0010 3e 4c 6f 64 67 69 6e 67 3c 2f 61 3e 20 2d 0a 3c >Lodging</a> -.<
(blah, blah, blah...)
0530 3c 61 20 68 72 65 66 3d 72 2f 63 70 3e 43 6f 6d <a href=r/cp>Com
0540 70 61 6e 79 20 49 6e 66 6f 3c 2f 61 3e 20 2d 0a pany Info</a> -.
Frame 45 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906354783
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906354783
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x16d2 (incorrect, should be 0x2eda)
|
Frame 46 (341 on wire, 341 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906354783, Ack: 1166525632
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906354783
Next sequence number: 906355070
Acknowledgement number: 1166525632
Header length: 20 bytes
Flags: 0x0019 (FIN, PSH, ACK)
Window size: 17680
Checksum: 0x05b9 (correct)
Hypertext Transfer Protocol
Data (287 bytes)
0000 3c 61 20 68 72 65 66 3d 72 2f 63 79 3e 43 6f 70 <a href=r/cy>Cop
0010 79 72 69 67 68 74 20 50 6f 6c 69 63 79 3c 2f 61 yright Policy</a
(blah, blah, blah...)
0100 3c 2f 66 6f 72 6d 3e 3c 2f 63 65 6e 74 65 72 3e </form></center>
0110 3c 2f 62 6f 64 79 3e 3c 2f 68 74 6d 6c 3e 0a </body></html>.
|
Frame 47 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906355071
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906355071
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17393
Checksum: 0x16d2 (incorrect, should be 0x2ed9)
|
Frame 48 (60 on wire, 60 captured)
Ethernet II
Internet Protocol, Src Addr: a32.g.a.yimg.com (24.94.162.91), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1080 (1080), Seq: 3443607971, Ack: 1166630548
Source port: http (80)
Destination port: 1080 (1080)
Sequence number: 3443607971
Acknowledgement number: 1166630548
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 32376
Checksum: 0x2d7a (correct)
Frame 49 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: a32.g.a.yimg.com (24.94.162.91), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1080 (1080), Seq: 3443607971, Ack: 1166630548
Source port: http (80)
Destination port: 1080 (1080)
Sequence number: 3443607971
Next sequence number: 3443609331
Acknowledgement number: 1166630548
Header length: 20 bytes
Flags: 0x0018 (PSH, ACK)
Window size: 32640
Checksum: 0x701a (correct)
Socks Protocol
Frame 50 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: a32.g.a.yimg.com (24.94.162.91), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1080 (1080), Seq: 3443609331, Ack: 1166630548
Source port: http (80)
Destination port: 1080 (1080)
Sequence number: 3443609331
Next sequence number: 3443610691
Acknowledgement number: 1166630548
Header length: 20 bytes
Flags: 0x0018 (PSH, ACK)
Window size: 32640
Checksum: 0xb0b1 (correct)
Socks Protocol
Frame 51 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: a32.g.a.yimg.com (24.94.162.91)
Transmission Control Protocol, Src Port: 1080 (1080), Dst Port: http (80), Seq: 1166630548, Ack: 3443610691
Source port: 1080 (1080)
Destination port: http (80)
Sequence number: 1166630548
Acknowledgement number: 3443610691
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x4472 (incorrect, should be 0x5c42)
Frame 52 (1414 on wire, 1414 captured)
Ethernet II
Internet Protocol, Src Addr: a32.g.a.yimg.com (24.94.162.91), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1080 (1080), Seq: 3443610691, Ack: 1166630548
Source port: http (80)
Destination port: 1080 (1080)
Sequence number: 3443610691
Next sequence number: 3443612051
Acknowledgement number: 1166630548
Header length: 20 bytes
Flags: 0x0018 (PSH, ACK)
Window size: 32640
Checksum: 0x7430 (correct)
Socks Protocol
|
Frame 53 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: www.yahoo.akadns.net (64.58.76.223)
Transmission Control Protocol, Src Port: 1078 (1078), Dst Port: http (80), Seq: 1166525632, Ack: 906355071
Source port: 1078 (1078)
Destination port: http (80)
Sequence number: 1166525632
Acknowledgement number: 906355071
Header length: 20 bytes
Flags: 0x0011 (FIN, ACK)
Window size: 17393
Checksum: 0x16d2 (incorrect, should be 0x2ed8)
Frame 54 (683 on wire, 683 captured)
Ethernet II
Internet Protocol, Src Addr: a32.g.a.yimg.com (24.94.162.91), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1080 (1080), Seq: 3443612051, Ack: 1166630548
Source port: http (80)
Destination port: 1080 (1080)
Sequence number: 3443612051
Next sequence number: 3443612680
Acknowledgement number: 1166630548
Header length: 20 bytes
Flags: 0x0018 (PSH, ACK)
Window size: 32640
Checksum: 0xd01e (correct)
Socks Protocol
Frame 55 (54 on wire, 54 captured)
Ethernet II
Internet Protocol, Src Addr: DBANTTARI (65.28.72.130), Dst Addr: a32.g.a.yimg.com (24.94.162.91)
Transmission Control Protocol, Src Port: 1080 (1080), Dst Port: http (80), Seq: 1166630548, Ack: 3443612680
Source port: 1080 (1080)
Destination port: http (80)
Sequence number: 1166630548
Acknowledgement number: 3443612680
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x4472 (incorrect, should be 0x547d)
|
Frame 56 (60 on wire, 60 captured)
Ethernet II
Internet Protocol, Src Addr: www.yahoo.akadns.net (64.58.76.223), Dst Addr: DBANTTARI (65.28.72.130)
Transmission Control Protocol, Src Port: http (80), Dst Port: 1078 (1078), Seq: 906355071, Ack: 1166525633
Source port: http (80)
Destination port: 1078 (1078)
Sequence number: 906355071
Acknowledgement number: 1166525633
Header length: 20 bytes
Flags: 0x0010 (ACK)
Window size: 17680
Checksum: 0x2db9 (correct)
|
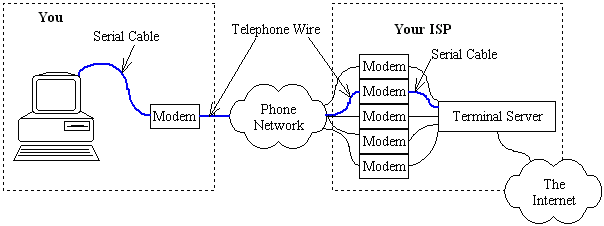 Image created using SmartDraw. Click Here for a free trial copy. |
| The following are questions submitted to me via e-mail.
The answers may not always be complete, and quite often there are
unmentioned exceptions (that, of course, prove the rule :-)
As usual, use any information here at your own risk; I am not responsible if any errors or omissions that adversely affect you. If you submit a question to me, please include whatever details you can to help me answer. I don't guarantee a response; if I do respond, I may post the response here, without your full name, edited for brevity, and after altering any IP addresses to preserve your anonymity. |
| Question added 6/8/2001, submitted by Manoj |
| Q: Can you please tell the differences between logical port and physical port? |
| A: Think of a logical port as a "software" port and a physical
port as a "hardware" port. For example, if you have a Frame Relay T1 line
installed so that you can commumicate with 5 branch offices, each of the 5
virtual circuits are terminated at a logical port, yet there is only one
physical T1 port on the router. Every physical port has at least one logical port associated with it (unless it's disabled.) |
| Question added 12/1/2000, submitted by Suraj |
| Q: Can you explain to me the concept of "SUPERNETTING" with a good
example? |
| A: "Supernetting" is really a term that predates RFC 1812, and
refers to the practice of combining multiple contiguous "classfull"
networks into a larger subnet than RFC 950 would allow. For example, you could combine the networks 192.168.2.0/24 and 192.168.3.0/24 into one network 192.168.2.0/23 (note the 23), but RFC 950 does not allow for "Class C" addresses to have a subnet mask of less than 24 bits. RFC 1812, however, removes the class restrictions from networks, and therefore effectively obsoleted the term "supernetting." Technically, RFC 1812 also obsoletes the term "subnet mask" and replaces it with the term "network prefix", but it's a distinction that is rarely made. |
| Question added 10/15/2000, submitted by Shaowu |
| Q: I was wondering if you would like to give me some ideas about
the following question? Consider that a host, say A, of IP address in class B and the subnet mask "255.255.0.0", and a host, say B, of IP address in class C and the subnet mask "255.255.255.0". Assuming that the host A and host B can "ping" each other. After changing the subnet mask of the node B to "255.255.0.0" (just done on the host B), could host A and host B "ping" each other? If not, how to let them "ping" each other with the codition that they keep their original IP address and use the same subnet mask "255.255.0.0"? |
| A: As long as the subnets don't overlap, and the routing is
properly configured (which it is if you can ping each other), then you're
fine. Remember, you only know (or care) what the destination subnet mask
is if the destination subnet also happens to be the source
subnet. The first routing decision is made by the sender, and that decision is whether to send the packet to the router, or to send it directly to the destination host (if the sender determines that both machines are on the same subnet.) As long as the routing is properly configured on both sides, you'll be fine. In fact, many misconfigurations will work fine, too, if a touch inefficiently. If you use a subnet mask that is too specific, you may wind up sending many packets destined for local hosts to the router, which then will put the packets right back on the same wire back to the local destination. If your subnet mask is too broad, then you won't be able to reach any hosts on non-local subnets included in the overly broad mask (since the packets won't be sent to the router for delivery.) The goal of routing is to eventually get the packet to a router that is on the same subnet as the destination. Play with the subnet calculator a bit to see that first routing decision in action. |
| Question added 6/13/2000, submitted by Victor |
| Q: What does a company like yahoo do when they receive too many hits on their single IP address. Do they just get a bigger router? i.e. Two routers on the net cannot have the same IP address which implies they just have to upgrade to a bigger router, they can't just add another. Also, what if the servers behind the router use up all the port numbers? Does this mean that no more servers can hide behind the single IP address? I've just been really curious how the major internet companies scale their networks to handle thousands of transactions and users. |
A: First, remember that there can be a one-to-many relationship
between names and IP addresses, and with hardware assistance, between IP
addresses and servers. For example, www.microsoft.com maps to five
different IP addresses:
C:\>nslookup www.microsoft.comAdditionally, each of those IP addresses probably represents whole cluster of Web servers hidden behind a hardware device such as Cisco's Local Director. Remember, it's the Web servers doing the bulk of the work; routing is relatively simple by comparison. Building a database cluster to handle that page request load is another feat. The two flaws in the question: first, a DNS name can (and often does) point to multiple IP addresses, which facilitates running many servers in parallel to handle very large loads; second, it's not the routers that are problematic in handling significant loads-- generally speaking, Web site capacity planning focuses on the database and Web server(s), not the router(s). |
| Question added 3/21/2000, submitted by Kathy |
| Q: I have been trying for several months to find information on tracking the origin of an e-mail thru the message ID, I have had no success. Do you know of a way to track if so can you share that information or is this considered a trade secret??????? |
| A: No secrets here :-) You can find out much about the origin of a message by the headers. The following are the headers from a SPAM letter I got the other day (you may need to find a "view headers" option in your e-mail client to view these on your own messages):
What we're seeing here (read the Received: lines from bottom to top) is that someone at 198.144.76.204 (which has a DNS name of pt-006-00189.greenapple.com) used the mail server rech1.werbebuero1.de (195.90.0.60) to relay SPAM to me. I would notify abuse@greenapple.com and postmaster@greenapple.com that a customer was sending SPAM from their network, and I would notify abuse@werbebuero1.de and postmaster@werbebuero1.de that their mail server was misconfigured and being used to relay SPAM, thereby filling up their mail queue and causing mail delays for their important mail, using all their expensive bandwidth, etc... Note that the From: address is probably forged/fraudulent, and the To: address has nothing to do with who the mail was sent to. The from, to, and reply-to headers are created by the sender; the commands that indicate who the /real/ recipient is don't get included in the actual message. Note that it's a trivial matter to forge un-digitally-signed e-mail from and to someone. Fortunately, the intermediate mail servers generally always include the IP address of the source of the e-mail. If that can be tracked (with help from the date/time stamp) to a sender, you can find the exact individual who sent the e-mail. If you require secure communications with someone, look into PGP at http://web.mit.edu/network/pgp.html. It is a system that can prove a message is from a certain sender and has not been tampered with (digital signature) and, optionally, it can also encrypt the message so that only the sender's designated recipients can read it (though they also need PGP to either verify the signature or decrypt the message.) It's free for personal use, and businesses need to pay a reasonable fee. For an excellent document on how PGP works, see http://www.pgpi.org/doc/pgpintro/. |
| Question added 3/2/2000, submitted by Luis |
| Q: If host A wants to PING host B which is 3 routers away, host A
must ARP for his gateway (router). Once he gets the MAC for the gateway,
host A sends the packet to the gateway ( we know it did a Boolean "AND"
and determined that the "pinged" IP address was not local. My question is
this: When the router closest to host A (his gateway) receives the packet and realizes that he does have a route to host B, does the packet leaving router have as a source IP that of the router itself or the IP of the host A???? |
| A: The layer 3 source and destination IP address do not change between the source and destination, unless you have a firewall in between performing Network Address Translation. The layer 2 information, however, is stripped off and replaced at every hop. If a packet traverses an Ethernet network to the first router, a PPP link to another router, and reaches a destination on a Token-Ring network, then the packet will have a destination MAC address of the first router for the first hop, no destination MAC address for the second hop (since PPP is point-to-point, it doesn't need to specify which machine is supposed to get the packet), and the third hop will have a Token-Ring header with a source MAC address of the router, and destination MAC address of the target machine. At no point do the source and destination machines know anything about the layer 2 configuration of each other (unless they're on the same subnet.) |
| Question added 3/1/2000, submitted by Sid |
| Q: This is a great and very useful source of information.
[Thanks!] I still don't completely understand TCP/IP subnets and
submasking, but this really helps. Hopefully, after I've read it a few
more times, I'll find the answer to my question: do all hosts on a LAN
need to have the same submask setting? |
| A: All hosts on a given LAN subnet must share the same
mask. The subnet mask, when applied to the host's IP address, indicates
which other IP addresses should be on the same network. Packets sent to
destinations not believed to be on the same network are sent via the best
available route-- usually to the default router. An easy way to theoretically disconnect yourself from the world is to set a subnet mask for your workstation that suggests that your default router is on a different network. If you can't send packets to your default router, then you can't talk to anyone not on your subnet. (I've noticed, however, that Windows machines will attempt to ARP the Ethernet address for any IP address given to Windows as the default router's IP address. So, in this case, if the default router is physically on the same network, even if it's logically seperate, it will work.) To see the subnet mask in action, refer to Daryl's Subnet Calculator (heh.. someday I'll come up with a more creative name), at http://ipprimer.windsorcs.com/subnet.html |
| Question added 6/5/1999, submitted by Kent |
| Q: This is a great site. Thank You. [You're welcome.] I do have one question concerning subnetting and when to do so. How many nodes can you put on one TCP/IP subnet before it requires segmenting your network? I am referring to a Lan with approx. 300 users. Is there a reason why I can't use a standard 255.255.000.000 subnet. I will only be assigning addresses in my DHCP scope as the network requires them. |
| A: This is a good question, and really is more of a layer two
question than a TCP/IP question. I would not run a 300 user lan on a
single 10Mbps Ethernet segment; however, I wouldn't balk at a 300 user
network segmented into 12 or 24 switched partitions using a centralized
Ethernet switch. So the real question here is, "will my current layer two
network topology support 300 users on one segment?" You can put as many
nodes as you want on one TCP/IP segment; however, that lack of limitation
does not apply to Ethernet. (I would ensure no Windows boxes are running
NetBEUI, though.) Remember, a switch "segments" networks on layer two, and a router "segments" on layer three. The main difference, from a topology planning standpoint, is that switches forward broadcast packets and routers don't. Thus, switching becomes a problem quickly with "loud" protocols like NetBEUI, since switching doesn't reduce or segment broadcast traffic. You can use a subnet mask of 255.255.0.0 to put up to 65,534 hosts on a single routed network segment; or you can use a subnet mask of 255.255.254.0 to put up to 512 hosts on a network segment. I'm assuming you're using "reserved" addresses (such as 10.1.x.x) behind a NAT firewall or proxy, so the choice of subnet mask is yours. The choice of whether or not to segment by switching or routing is also yours; I tend to prefer switching, since it tends to keep things simpler. |
| Question added 1/23/1999, submitted by NBK |
| Q: How vulnerable is Linux against Net attacks compared to NT???
Damn NT has to many holes.... |
| A: In both cases, it depends on the administrator :-) a good packet filter or (better yet) firewall, good knowledge of the security issues of the services the box is providing, and keeping current on the security updates/mailing lists for the OS'es and running services makes for a pretty strong box. Any badly installed service can present the opportunity for a full breach; be sure to read the security FAQ's (and I'll often scan cracker websites) for the OS and the services you're making available to the public. |
| Question added 12/3/1998, submitted by David |
| Q: This is to request from you a tutorial on TCP/IP. Thank you very much. [Answer: can you be more specific? Platform, etc?] Actually I'm looking for an overview on the internet network. How the providers build their network... How do they get inteconnections... What are the critical economical issues for internet on the next years...etc |
| A: Hm... That's intentionally outside the scope of the Primer
(hence the subtitle, "...the near side of the 'net.") For the information
you're looking for, search for "BGP4" re: interconnections, and regarding
economic issues (etc) try any of the Internet trade rags for the
professional pundits :-) Doing generic dialup and hosting does not (IMHO) have an entry level any more; the services are very commoditized and the economies of scale involved will squeeze out the smaller non-value-added providers. But (apologies to Dennis Miller) that's just my opinion, I could be wrong. |
| Question added 10/12/1998, submitted by Joanne |
| Q: The part I don't understand is: what is the reason to subnet?
You can't possibly get more destinations that way, I mean, 32 bits are 32
bits. There's only 4 billion possible internet destinations, no matter how
you split it up. So what does subnetting do for ya? |
| A: Subnetting does two things, depending on what context you're
in: If you're a workstation (or server), the subnet mask is used to determine whether the destination IP address is on your same subnet; if so, the workstation will attempt to ARP the destination's Ethernet card address and deliver the data directly; remember, the first routing decision is made by the workstation, and the decision is: whether or not to send the packet to a router. Routers keep their routing tables managable by clumping large blocks of addresses together using broad subnet masks ("Network Prefixes"). In the old days of classful routing, routers would have to keep track of each "Class C" address individually, which was causing extreme growth of routing tables; CIDR routing allows you to clump as many "Class C" networks together as you want (in powers of 2.) So, you may ask, what about servers that also act as routers? In which category to they fall? Well, I lied when I said that subnetting does different things depending on context; it's just that most IP end stations (workstations) don't bother trying to keep track of the whole network; they just know that "these addresses are local, and I'll send anything else to my default gateway/router." |
| Question added 10/6/1998, submitted by Bob |
| Q: Is it possible with IE or netscape to address a web server by
its MAC address? |
| A: It sounds like you're asking if you could run HTTP over DLC;
the short answer is "no." The long answer: the HTTP protocol is based on the TCP protocol, which is based on IP; therefore, both the client and server must already be running IP for HTTP to work. You could force client and server IP address into their local ARP caches if they are on the same subnetwork (bounded by routers), but I dont know how well that would work (I doubt the IP stack checks its arp cache before it determines whether or not a given IP is on a locally attached subnet.) If it did work, you could then type the (fake?) IP address of the server into your browser's location line to pull pages. The server would then reply to your (fake?) IP address. Alternatively, if there is an IP router involved, you could play with its ARP cache; routers are more likely to be forgiving about having multiple IP subnets (or, network prefixes, in RFC 1812 parlance) on the same subnetwork than, say, Win95 workstations. Note that on any point-to-multipoint network (like Ethernet or Token Ring, but not including serial PPP or HDLC connections), the most basic address (in the layer 2 MAC header) is the MAC address. But you cannot type a MAC address into 'IE or netscape' and connect to a web server; even if you could, the web server would not know what IP address nor TCP socket number to reply to. |
| Question added 9/30/1998, submitted by Jim |
| Q: I just have a quick question, its regarding Windows 95 (Yeah, I hear you screaming), when you set the computer to 'disable DNS', and don't set a gateway address (all via control panel) and disable WINS--how is anything assigned to the computer? Is it fair to assume its BOOTP, or something else? |
| A: Probably DHCP; BOOTP assigns the IP address, subnet mask, default gateway (route), and (if memory serves) the DNS information. DHCP allows for a bunch of other information to be sent to the workstation, including WINS server addresses. DHCP also has a facility for "lease expiration", where addresses that are not renewed are returned to the pool of available addresses; under BOOTP, IP addresses are permanently associated with the NIC's MAC address, so if you throw out the NIC, the IP address is "lost." Win95 does not support BOOTP. DHCP and WINS are two very different things, they just seemed to "appear" at the same time (with the introduction and subsequent popularity of Windows 95 and NT Server 3.5x). DHCP is used for automatically configuring workstations with all the information they need to access the TCP/IP resources available to them, including IP address, subnet mask, default gateway, and on Windows NT networks, WINS server addresses. WINS is like DNS for NT networks; WINS is used to "advertise" and locate NT server and (win95|nt) workstation resources on the NT network, such as shared drives and printers. DHCP is a non-Microsoft-specific "upgrade" to BOOTP, WINS can be described as a Microsoft Networking version of DNS. (Novell's version of WINS for distributing SAP information is called DSS, or Domain SAP Server.) BTW-- Win95 doesn't make me scream, but don't bring any Win3.X machines by unless you're equipped with earplugs :-) |
On the 'net: (in no particular order)
The Internet.com
Webopedia: The top non-search engine referrer of people to Daryl's TCP/IP
Primer. It must be a good resource. ;-)
The IP Address Guide: Web-based IP
address and domain name tools for Ping, Traceroute, NSLookup, CIDR, geolocation
and an HTML Validator.
The
Information Technology Professional's Resource Center: Well-organized set of
links to other TCP/IP resources. Not for the weak of vision-- everything is
<font size=1>
The IT Web Links Pages -
Protocols: Links to other information on TCP/IP
Uri's TCP/IP Resources
List: 'This posting contains a list of various resources (books, web sites,
FAQs, newsgroups, and useful net techniques) intended to help a newbie to learn
about the TCP/IP suite of protocols.'
Patrick's MCSE Place: Lots of MCSE stuff,
links.
Google's
Directory Service: the "best" links to networking resources. Too bad they
don't acknowledge my requests to fix their link to me. >:-(
| In Print: (with convenient
links to purchase the books from Fatbrain.com) This is a look at my bookshelf- I have included all of the books with more than one crease in the binding. |
| Topic | Recommendation |
|---|---|
| Setting up UNIX services for the Internet, including
details on TCP/IP and TCP/IP services like DNS and SENDMAIL. Helpful, even if you never touch UNIX. |
TCP/IP
Network Administration by Craig Hunt Published by O'Reilly and Associates, Inc. |
| Everything you ever needed to know about DNS. Referred to as the "DNS Bible" or simply "The DNS Book" on DNS mailing lists. | DNS
and BIND by Paul Albitz, Cricket Liu, Mike Loukides Published by O'Reilly and Associates, Inc. |
| Packet filtering and general Internet security | Building
Internet Firewalls by D. Brent Chapman, Elizabeth D. Zwicky, Deborah Russell Published by O'Reilly and Associates, Inc. |
| UNIX System Administration. Covers issues with several *nix flavors. | Essential
System Administration : Help for Unix System Administrators by AEleen Frisch Published by O'Reilly and Associates, Inc. |
| My Linux command reference. Always at my elbow when I'm doing anything interesting on my Linux box. | Linux
in a Nutshell by Jessica Perry Hekman, Andy Oram (Ed) Published by O'Reilly and Associates, Inc. |
| High speed Internet connectivity | Getting
Connected : The Internet at 56K and Up by Kevin Dowd, Mike Loukides Published by O'Reilly and Associates, Inc. |
| JavaScript: This book had everything I needed to make the Subnet Calculator work. | Javascript
: The Definitive Guide by David Flanagan Published by O'Reilly and Associates, Inc. |
| Interdomain (Backbone) routing-- how the big boys and girls do it. | Internet
Routing Architectures by Bassam Halabi Published by Cisco Press |
| Or, check out FatBrain's category for Computing & Internet Subjects : Networking & Telecommunications : Protocols & Standards : TCP/IP | |
| Other Favorites | |
| The first book I reach for when I have a question about how my favorite DBMS, Microsoft SQL Server, works. I was ready to leave NT behind and switch to ColdFusion/Linux (from ColdFusion/NT) when SQL Server 7.0 came out. | Inside
Microsoft SQL Server 2000 By Kalen Delaney,Ron Soukup Published by Microsoft Press |
| A must-read for any person who manages software development. The source of the oft-quoted "Brooks' Law": 'Adding manpower to a late software project makes it later.' | The
Mythical Man-Month By Frederick P. Brooks Jr. Published by Addison Wesley Longman |
| Although I prefer ColdFusion for Database-To-Web projects, Java occaisonally fits the bill when heavy lifting is required. At the time of this writing, there are nineteen books on ColdFusion listed at Fatbrain, but I can't personally recommend any of them-- probably because I've been using CF since version 2.0 and simply don't need to be told how CF works. | Java
Servlets By Karl Moss Published by Osborne/McGraw-Hill |
| JDBC and Java: Complete. Consise. What would we do without O'Reilly? | Database
Programming with JDBC and Java By George Reese,Andy Oram (Editor) Published by O'Reilly and Associates, Inc. |
| "A" Record | |
|---|---|
| |
| Address Lookup | |
| see Domain Name Service. | |
| Address Resolution Protocol (ARP) | |
| |
| ARP | |
| see Address Resolution Protocol | |
| Banana | |
| |
| Class | |
| |
| DNS | |
| see Domain Name Service. | |
| Domain Name Service (DNS) | |
| |
| Host | |
| |
| Interface | |
| |
| Internet Protocol (the IP in TCP/IP) | |
| |
| Internet Service Provider | |
| |
| Internetwork Packet eXchange (IPX) | |
| |
| IP | |
| see Internet Protocol. | |
| IPX | |
| see Internetwork Packet eXchange (IPX). | |
| ISP | |
| see Internet Service Provider. | |
| Layer 1 | |
| |
| Layer 2 | |
| |
| Layer 3 | |
| |
| "MX" Record | |
| |
| Name Resolution | |
| see Domain Name Service. | |
| Network | |
| see Segment | |
| Network Mask | |
| |
| Network Prefix | |
| |
| Protocol Stack | |
| |
| Router | |
| |
| Routing | |
| |
| Segment | |
| |
| TCP/IP | |
| |
| WAN | |
| see Wide Area Network | |
| Wide Area Network (WAN) | |
| |