Digital Signatures on Mobile Devices - Reality CheckBy Tao Huang, senior developer at Cysive, Inc. (http://www.cysive.com/), May 02, 2002Wireless technology offers mobile users the promise of easy access to valuable information and transactions when and where they want. However, security and privacy concerns must be addressed before meaningful, mass-appeal applications can be mobilized. Digital signatures provide authentication, data integrity and non-repudiation services to the mobile computing environment, but not without risk and cost. This article explains how digital signatures can be used to secure mobile applications, and discusses the current technical, regulatory and legal concerns associated with this technology. Mobile devices such as cellular phones, personal digital assistants (PDAs), and pagers have become an essential part of our lives. This wireless “revolution” is changing how, when, and where business gets done. We have the capability to attend to business or personal matters while on a plane, at the park, or in line at a grocery store. But the first wave of mass-market mobile applications has ebbed, leaving little in its wake but a handful of consumer-oriented novelties (e.g. PIM, wireless e-mail, the wireless web), while questions of privacy and security still hamper widespread adoption of “real” mobile applications. Without a satisfactory solution to this problem, mobile applications will never transcend their current novelty status. Mobile Transactions Must Be SecureBefore people feel confident to use mobile applications such as banking, brokerage or retailing, wireless security must be at an acceptable level. Wireless security is critical in conducting complex, high value transactions and enterprise specific applications. The traditional threats to wireless communication include interception of data on the air interface, compromised confidentiality of data, etc [1]. In a wireless network, security policies can be set for different protocol stacks (physical layer, transport layer, etc). Digital signatures provide unique security services to mobile devices at the application layer.How Digital Signatures WorkDigital signatures take advantage of public-key cryptography. The signer’s private key is used to encipher, or “sign” a message. A digital signature is a piece of data that accompanies the digitally signed message. The singer’s public key can be retrieved from a certificate issued by a Certificate Authority. The public key can then be used to decipher the message and verify the signature. This is illustrated in figure 1. Digital signatures offer the following security services.
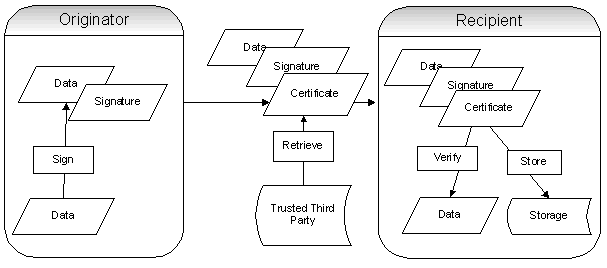 Figure 1. Digital Signature Generally, we refer to the attribute of non-repudiation of a communication as non-repudiation of origin. It aids resolution of disagreements over whether or not a particular party originated a particular message, the time this origination occurred, or both [2]. Digital signatures can make m-commerce transactions smoother, more secure, and less expensive, especially for those things that require lots of paperwork and paper signatures. Here is a simple example. Assume an individual has an account at an on-line brokerage. The individual buys 100 shares of some stock by using and application on his mobile phone, then subsequently denies that he bought them. It’s difficult for the on-line broker to prove that the individual did indeed buy those shares, especially in court. But if the application uses a digital signature when the trade is requested, the on-line broker can easily verify the transaction. The Essential PiecesThe use of digital signatures needs the technological and legal framework provided by a public-key infrastructure (PKI). This includes the certification authorities (CAs), repositories associated with CAs, registration authorities (RAs), etc [3]. This is illustrated in figure 2. RAs validate, approve or reject certificate requests and do the subjects authentication. After issuing the certificates, CAs may publish the certificates to a certificate repository, such as a directory service. The distribution of signers’ public keys is in the form of certificates. Many PKIs have been successfully deployed. VeriSign, Inc. maintains the largest commercial certification authority network, the VeriSign Trust Network.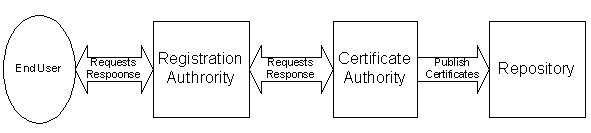 Figure 2. Main components of Public-Key Infrastructure Legal ConsiderationsBefore digital signature technology can be fully exploited, its legal uncertainties must be addressed. The Federal Electronic Signatures in Global and National Commerce Act (aka the E-Sign Act) was signed on June 30, 2000 and took effect in October 2000. The E-Sign Act allows e-signatures to be as legally binding as handwritten signatures for e-commerce transactions.The E-Sign Act doesn't dictate what technology must be used to implement e-signatures. It broadly defines an electronic signature as “an electronic sound, symbol or process” executed or adopted with the intent to sign a contract or record” [4]. Warwick Ford analyzed some of the issues of the E-Sign Act [5]. The most important one is that the Federal E-Sign Act’s preemption provisions are broad and would therefore preempt most, if not all, of the digital signature laws in the various U.S. states, fostering conflict between state and federal regulations. Over the next twenty years, evolving regulations and policies will shape the development of the wireless industry [6]. Technical ConsiderationsThe widespread deployment of digital signature technology depends not only on the resolution of legal uncertainties, but also on the resolution of technical issues. One of the main security initiatives for mobile phones is Wireless Applications Protocol (WAP) [7]. The WAP security model consists of four main components: Wireless Transport Layer Security (WTLS), Wireless Identity Module (WIM) [8], WMLScript Crypto Library, and WAP Public Key Infrastructure (WPKI). Several commercial firms have implemented WTLS, including RSA Security, VeriSign, and Certicom. WIM is closely related to the digital signature support in the mobile phone arena. An example of a WIM implementation is a smart card, which has an embedded microprocessor chip. In the phone, it can be the Subscriber Identity Module (SIM) card or an external smart card. For optimum security, the permanent private keys should be stored on the smart card based on the specification of the Wireless Identity Module. Then the private keys can be used in the WTLS handshake with client authentication, and for making application level digital signatures.Compared with mobile phones, today’s PDAs are far more capable. But there is no WAP-like standard to address the security issues related to PDAs; the security software space for wireless platforms is not that mature. Limited software products are available in the market. With PDAs, the principal security challenge is how to secure sensitive data, such as a password, in case a PDA is lost or stolen. Products like PDASecure from Trust Digital enable secure password and data encryption for Palm and Pocket PC devices. Unfortunately, even if the signer’s private key is stored on the PDA and protected using PDASecure, this secure schema cannot be considered as a Wireless Identity Module (WIM) implementation [8]; it is not completely tamper-resistant because there is no certain physical hardware protection used. The private keys need to be stored on a tamper-resistant device like a smart card. There are different digital signature cryptosystems [9]. RSA algorithm has tended to dominate the market. Compared with RSA, Digital Signature Algorithm (DSA) requires more processing- resource during verification process. Elliptic curve-based digital signature systems have more efficient implementations. They can generate and verify the digital signatures more quickly than RSA or DSA. A standard for the elliptic curve based algorithm is called the Elliptic Curve Digital Signature Algorithm (ECDSA). With faster processing speed and less resource requirements, Elliptic curve cryptosystems may be easily embedded in the smart cards, which perform the cryptographic operations for a WAP phone. The product, Certicom Trustpoint Client supports all of the three signature algorithms and the following PDA platforms: Microsoft Window CE 3.0 for PocketPC, Palm OS 3.5 and RIM Blackberry 2.0. Trustpoint Client can be used to build the digital signatures application for a PDA. What-You-See-Is-What-You-SignThere are other issues besides the legal and technical concerns discussed above [10]. One issue is related to the concept of “What-You-See-Is-What-You-Sign” (WYSIWYS). In a typical application, the data to be signed is displayed to the signer before he digitally signs it. It’s a function of the software application to accurately represent the data. An application programming oversight could result in the signing of invalid (or unseen) data. Another issue is related to the archive of the digital data and the data format. This is necessary for non-repudiation purposes. Sometimes, digital signatures need to be archived for a long period of time, so that they can be presented during legal proceedings if required. However, the current pace of technology evolution could render the data formats or storage media obsolete. The process of retrieving the data under these circumstances could be very expensive.SummaryCorporations face formidable challenges in implementing digital signatures; conflicting state and federal regulations, lack of interoperability among digital certificate vendors, technical complexity, and high deployment costs all contribute to a slow rate of adoption. Applying digital signatures to mobile devices introduces additional challenges, due to their limited bandwidth, memory, and processing capabilities. While the technology required to implement digital signatures has made great strides, digital signatures have a long way to go in order to become mainstream. And until that time, the promise of secure mobile applications will remain elusive.About the AuthorTao Huang is a senior developer at Cysive, Inc. based in Reston VA. Since joining Cysive in 1998, Tao has participated in developing digital signature for pocket pc, and is currently involved in the development of CymbioTM, Cysive’s J2EE-based Interaction Server product. Tao can be reached at thuang@cysive.com.References1. Randall K. Nicholes, Panos C. Lekkas, Wireless Security, McGraw-Hill, 2002, p. 62.2. Warwick Ford, Michael S. Baum, Secure Electronic Commerce, Prentice Hall PTR, 2001, p. 338. 3. Warwick Ford, Michael S. Baum, Secure Electronic Commerce, Prentice Hall PTR, 2001, p. 251. 4. Electronic Signatures in Global and National Commerce Act 5. Warwick Ford, Michael S. Baum, Secure Electronic Commerce, Prentice Hall PTR, 2001, p. 297. 6. Randall K. Nicholes, Panos C. Lekkas, Wireless Security, McGraw-Hill, 2002, p. 9. 7. Wireless Applications Protocol, http://www.wapforum.org 8. Wireless Identity Module, version 12-July-2001, http://www.wapforum.org 9. Randall K. Nicholes, Panos C. Lekkas, Wireless Security, McGraw-Hill, 2002, p. 110. 10. Mohan Atreya, Ben Hammond, Stephen Paine, Paul Starrett, Stephen Wu, Digital Signatures, McGraw-Hill, 2002, p. 112. Send details to editors@wirelessdevnet.com |